Anatomy of a Simple Brute Force CTF Challenge
This was originally a hackthebox.eu challenge therefore I have changed all relevant details that are part of solving the actual challenge.

Pre-Setup:
– Set up Burp Suite to use as proxy for Firefox. Tutorials available on google.
– Set up Kali Linux in a virtual machine for using Hydra.You can also install Hydra on Windows if you prefer.
Step 1: Finding the Right Tool!
A. Use Burp Suite to capture login request which is then sent to the Intruder (in Burp Suite) to then resend to the webserver using custom payloads e.g. passwords. I used a variety of lists and all in all tested around 1500 of the most common passwords with no results.
B. I then switched to a tool that could crack the login faster, Hydra. However, utilizing Hydra on a web login form was tricky.
Step 2: Getting the Syntax Right!
A. In order to issue the command correctly there were three custom parameters in addition to several mandatory ones. The optional parameters are separated by colons and enclosed in quotes, as follows;
“url of login form: parameters used in web request e.g username=^USER^&password=^PASS^: and finally the request returned by the website when the login fails e.g. Bad password.”
Furthermore…
The command “Hydra” starts the program
-s is used to designate the port you are attacking.
-l is used to set the username or -L can be used to point to a list of usernames in a directory on your hard drive.
-P is used to point to a list of passwords stored on your computer.
-t specifies the amount of threads to run at a single time (affects speed of cracking)
-m is placed before the optional parameters (see above, Step A) (ALWAYS PLACE OPTIONAL PARAMETERS IN QUOTES!)
The url you are attacking is listed next
Then finally list the service you are attacking e.g. http-get
For example:
hydra -s 55555 -l username -P /user/bob/passwordlist.txt -t 16 -m /:username=^USER^&password=^PASS^:Badpassword urloftargetsite.com http-get
Sidenote: I got a false positive response of 16 valid passwords using the above format before realizing I did not put the optional parameters in quotes and forgot to place a space between Badpassword (the exact response returned by the webpage after a failed login e.g. Bad password)
“hydra -s 55555 -l username -P /user/bob/passwordlist.txt -t 16 -m /:username=^USER^&password=^PASS^:Bad password urloftargetsite.com http-get”
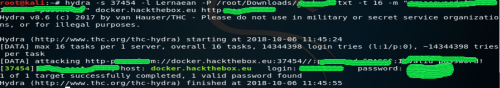
After correcting the syntax 1 valid password was returned.
3. Evaluate the response packet after entering in the correct password!
We can tell which portion of the response the flag is according to its format. “HTB{text_here}”. Here the flag was HTB{x9x9_8_5tf4_u5n}.
P.S. THIS IS NOT THE REAL FLAG.
